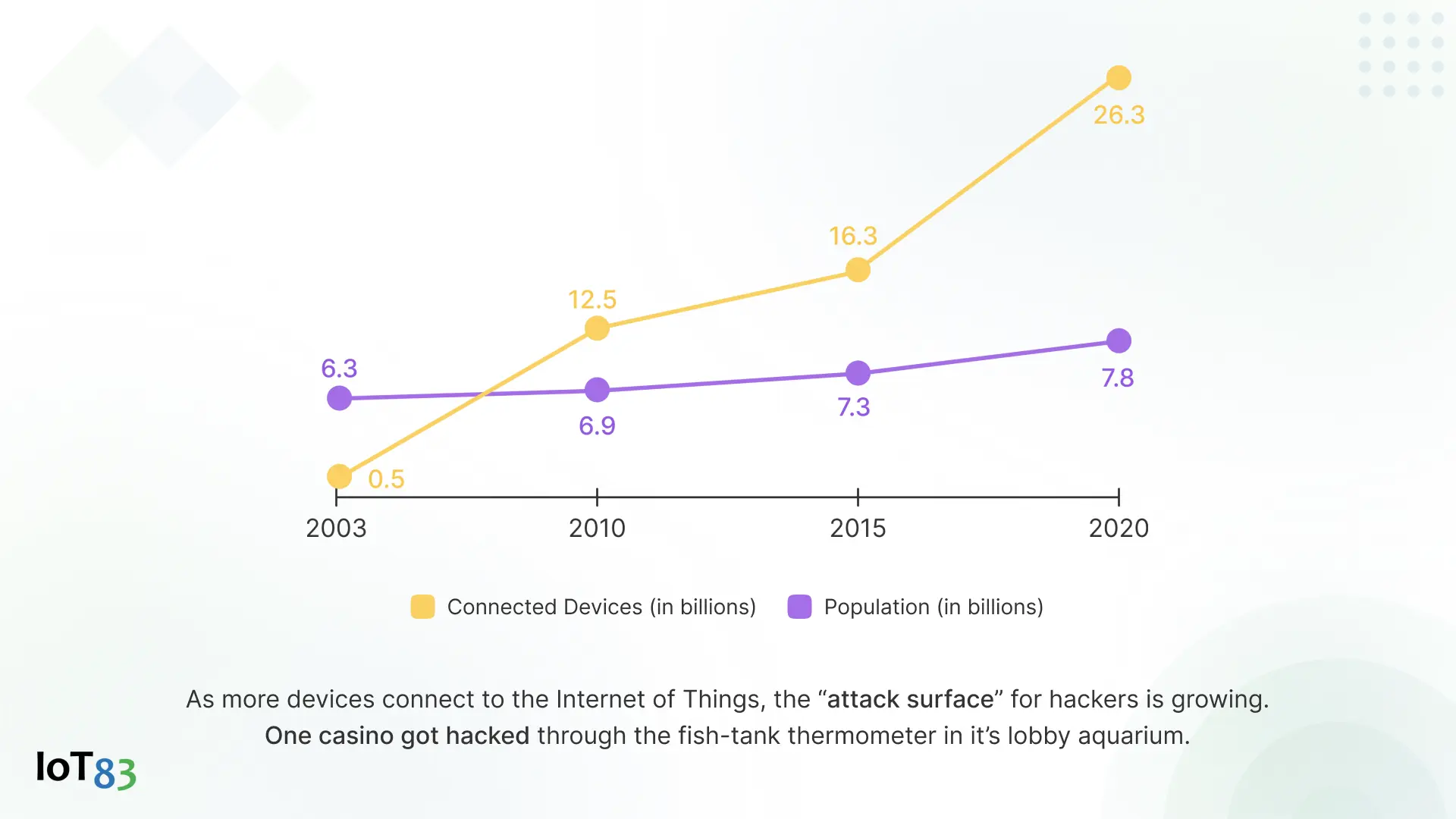
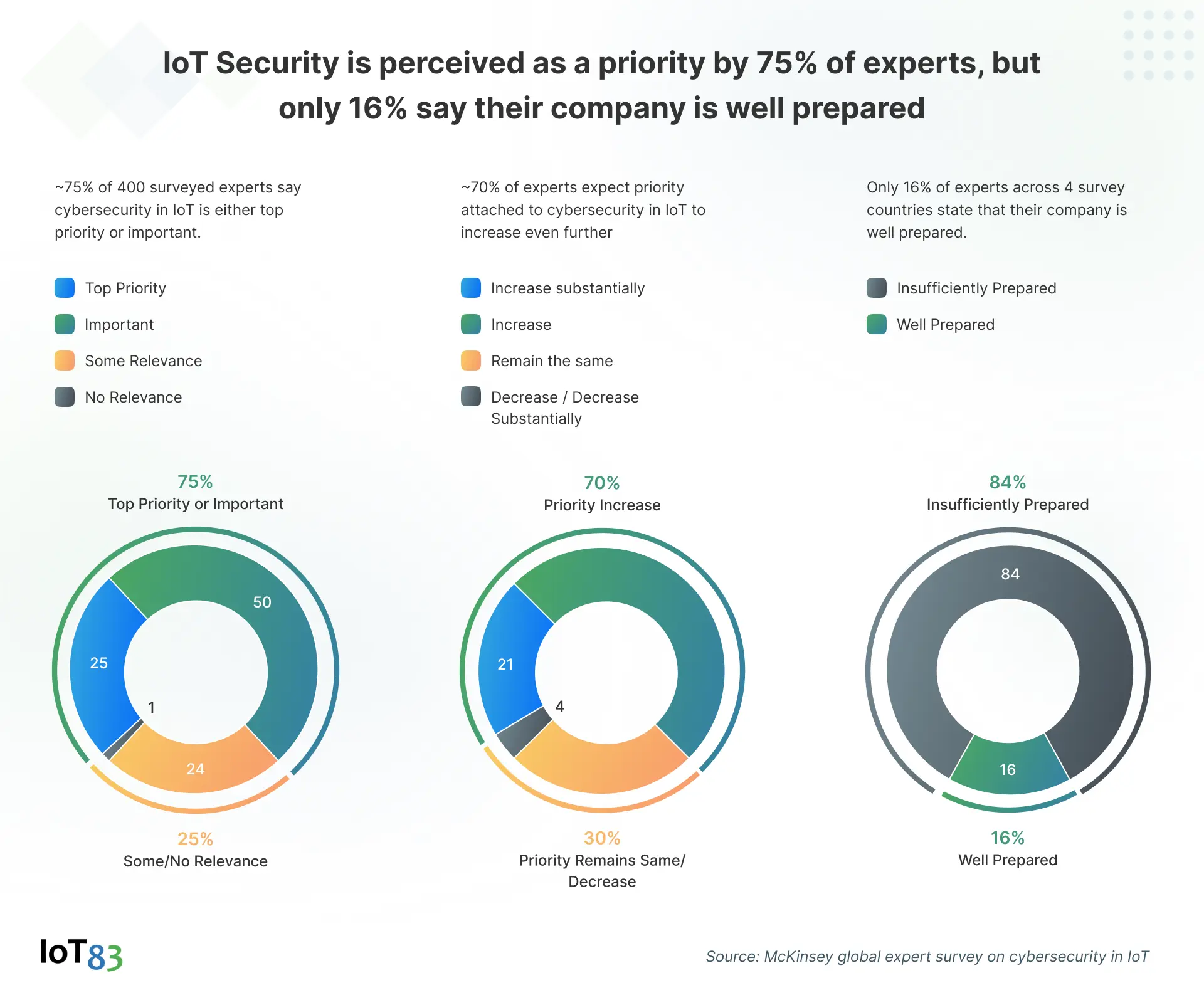
Whether you build or buy an Industrial IoT platform, there are two main aspects that worry every OEM. First are the requirements to maintain IoT cybersecurity in the platform. Keep track of the exponentially growing number of devices and volume of data. Not maintaining it well can be a breaching window for attackers.
Second, there are security capabilities, from asset management to smart dashboard analytics, that depend on industrial IoT platform providers.
What can you do as an individual or a firm if you are dependent on a platform provider for end-to-end IoT cybersecurity? Ensure your chosen platform has the best possible security approach while meeting your business requirements.
6 Questions to Ask Your Platform Partner for Efficient IoT Cybersecurity
How Can OEMs Monitor Devices with the Increasing Number?
As per the Cisco Survey, 58% of respondents said they want to gain comprehensive visibility on OT devices and industrial networks. Over time, OEMs end up with a collection of old and new devices connected to their network. Here, proper visibility is vital for maintaining an accurate inventory as well as preventing unmonitored devices from becoming entry points for attackers. An OEM Enterprise Domain Cloud (OEDC) shines in real-time remote device monitoring and management and can even boost your ability to get a secure and scalable solution.
Is Having an External System for IoT Cybersecurity an Issue?
IoT devices often lack the capability to integrate with existing security frameworks and tools, making it difficult to apply uniform security policies across all devices and platforms. It’s essential to have the ability to integrate any third-party systems or applications and tackle the ever-evolving IoT cybersecurity challenges within the infrastructure to ensure a seamless defense mechanism.
What About Access and IoT Cybersecurity with Integrated APIs?
OEMs must ensure an appropriately used API irrespective of a web interface or deploying their own micro-services. Extending and enhancing the user interface is beneficial for getting your own value added for your users. This is where OEMs can get a smarter solution by trying to twist the API to your specific needs. It may give you short-term benefits but can result in unintended outcomes, such as API Privilege Escalation, a major IoT cybersecurity threat.
Will It Be Easy to Manage Access and Restrictions for the Various Roles?
It is essential to define a list of features and functionalities your tenants can access on the IoT platform. This way, you can manage the multi-tenancy efficiently in your application. Also, you must ensure your IoT cybersecurity solution complies with your corporate standards. Hence, OEMs must check that their IoT platform provides integration with IAM to provide you with the complete freedom to allow or restrict any function for a specific role.
Continuous Integration and Continuous Deployment (CI/CD) practices are essential for ensuring the software development process incorporates IoT cybersecurity measures at every phase. Key aspects of CI/CD include:
- Secrets scans
- Code quality checks
- Code coverage analysis
- Scan third-party vulnerabilities
- Docker image scanning
Incorporating these CI/CD practices into the IoT development process helps in early detection and remediation of security issues, leading to more secure deployments. It is vital in an era where IoT devices are increasingly becoming targets for cyberattacks.
Secret scans help detect hard-coded repositories like passwords, API keys, and other data sources, preventing potential IoT cybersecurity breaches.
Code quality checks ensure that the code adheres to best practices and standards, reducing the risk of IoT cybersecurity vulnerabilities.
Code coverage analysis identifies untested parts of the code, which are potential risk areas for security weaknesses.
Scanning for third-party vulnerabilities is crucial since IoT solutions rely on external libraries and frameworks. These scans help identify and remediate known vulnerabilities before they can be exploited.
Docker image scanning and image checksum validation are vital for ensuring that the containers used in the IoT environment are free from vulnerabilities and have not been tampered with.
Is Your IoT Platform Provider a CVE Registered Partner?
CVE (Common Vulnerabilities and Exposures) registered partners are authorized organizations to assign CVE IDs to vulnerabilities affecting products within their scope. These partners have demonstrated their commitment to IoT cybersecurity by actively identifying, registering, and mitigating vulnerabilities. By partnering with a CVE-registered partner, you can ensure that your IoT platform is continually monitored for new vulnerabilities and that these vulnerabilities are formally recognized and documented.
 This partnership facilitates the swift identification and remediation of security issues, enhancing the overall security posture of your IoT environment. A CVE-registered partner can also provide valuable insights into emerging IoT cybersecurity trends and vulnerabilities, enabling you to address potential security challenges proactively. This collaboration ensures that your IoT devices and platforms are secure by design and remain secure throughout their lifecycle.
This partnership facilitates the swift identification and remediation of security issues, enhancing the overall security posture of your IoT environment. A CVE-registered partner can also provide valuable insights into emerging IoT cybersecurity trends and vulnerabilities, enabling you to address potential security challenges proactively. This collaboration ensures that your IoT devices and platforms are secure by design and remain secure throughout their lifecycle.
Conclusion
These measures protect your IoT environment from current threats and prepare you to respond effectively to evolving IoT cybersecurity challenges. As IoT innovations continue to grow, prioritizing cybersecurity in partnership with knowledgeable technology partners will be vital for maintaining the virtue and trustworthiness of IoT solutions.
In conclusion, IoT83 can be the right choice if you are concerned about IoT Cybersecurity. We have all the metrics mentioned above, including the CVE registration, and we are responsible for receiving, processing, and disclosing IoT83 products and solution-related IoT cybersecurity vulnerabilities. It is the designated window to release information about IoT83 product vulnerability. IoT83 encourages end-users, partners, suppliers, government agencies, vendors, industry associations, and independent researchers to report potential risks or vulnerabilities to PSIRT by email: security.officer@iot83.com

Nishant Puri, Co-Founder & CISO at IoT83
Nishant carries professional expertise in team collaboration and network security solutions. He excels at aligning the needs of key business stakeholders, including Sales, Marketing, and Product Engineering, with pragmatic and efficient approaches that meet both short-term and long-term strategic goals.
Before joining IoT83, Nishant held a leadership position at Cisco America Partners, where he led sales and technology solutions. He was also a frequent speaker for Cisco APO, showcasing his knowledge and experience in the field. Being a Cisco-certified Inter-Networking Expert in Security and Collaboration, Nishant brings a wealth of technical expertise to his role. He is also inclined to identify digital discontinuities and is adept at mapping out effective digital transformations.